Crisis Management: How to Navigate the New Frontier of Corporate Cybersecurity

Posted By Derek Delano on November 01, 2019
The world of crisis management has changed dramatically and continues to swiftly shift as what constitutes a crisis and how organizations respond both continue to evolve. From Target to Equifax to Capital One, high-profile hacks of the last few years have certainly made headlines. As technology advances, so too do the methods of cyber criminals and activists looking to exploit loopholes and weaknesses — forcing organizations to up the ante to prepare for those worst case scenarios.
That’s not to say that 20th century crises — natural disasters, financial impropriety, executive malfeasance, and data hacks — don’t require planning. However, a new breed of complex breaches that target corporations, cities, and even entire countries have communicators questioning whether their crisis plan needs an update. (Hint, they probably do.)
Pay the Ransom?
Earlier this year, the city of Baltimore fell victim to a ransomware attack that caused thousands of government employees to lose access to email and forced the shutdown of several online services used by residents every day. That’s why earlier this month, Baltimore approved the purchase of $20 million cyber insurance policy. The move is notable for a number of reasons. First, the sheer cost, which is significant. Yet despite that amount of coverage, it would have just barely covered the estimated $18 million in damages the city suffered in the ransomware attack that motivated this security upgrade.
More importantly, the investment is indicative of a growing trend of organizations buying cyber insurance. According to the 2019 Global Cyber Risk Perception Survey from Marsh and Microsoft, nearly 50% of respondents said they have purchased cyber insurance, up from 34% in 2017. With ransomware attacks on the rise across municipalities, healthcare, and higher education, more organizations in these sectors are choosing to let insurers pay the ransom, rather than bear the cost themselves.
Waiting for the Other Shoe (Cyber Attack) to Drop
In a surprise plot twist, when TOMS Shoes’ email list was breached in early October, the hacker was not out to hold data hostage or to steal customer identities. They simply wanted to send a positive message to TOMS customers:
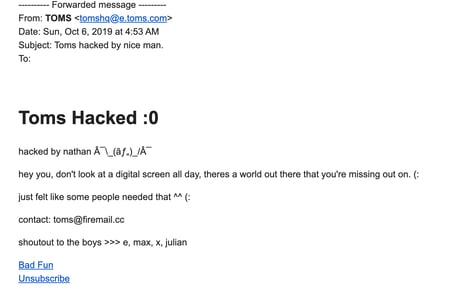 But while the intent may not have been malicious, it was an illegal hack nonetheless, and surely was unsettling to thousands of TOMS customers who received the email. TOMS likely has crisis plans in place, however it still took the company more than a day to communicate with concerned customers.
But while the intent may not have been malicious, it was an illegal hack nonetheless, and surely was unsettling to thousands of TOMS customers who received the email. TOMS likely has crisis plans in place, however it still took the company more than a day to communicate with concerned customers.
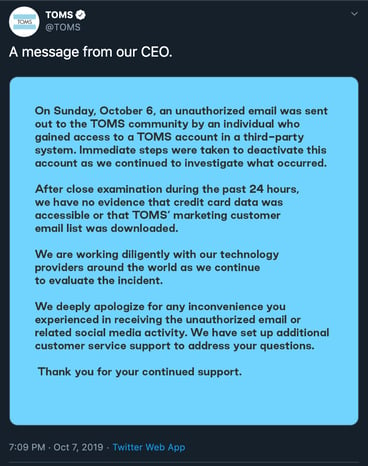
The ability to respond quickly and accurately is the whole point of having a crisis plan. While no customers were actually “harmed” in the TOMS hack, the brand suffered anyway because it took too long to respond. Although the attack’s timing certainly wasn’t ideal (it never is) and TOMS first needed to determine the scope and severity of the situation, a faster response could have been achieved with the right plan in place.
Hacker Hacks
So what lessons can be learned? For starters, if you think your crisis response plans are set and ready to go, think again. We don’t want to be alarmist, but the fact is, while the basic tenants of a good plan will always remain, crises have evolved. That’s been exemplified by the ransomware issue and also seen in the rise in fake news, more intense social activism, and a minute-by-minute newscycle. So if you haven’t taken an audit of your response plans, it’s time to ask your team these questions:
1. Have we planned for the right scenarios?
Many crisis plans envision a broad range of scenarios, but you need to be certain they are the right ones for your business. Ensure they truly prepare you to respond as immediately as possible to any crisis.
2. Have we conducted a simulation?
You may have the greatest crisis plan in the history of crisis plans, but if the stakeholders you count on don’t know the requirements and process, then it’s of limited use. Teams from across your organization will play a critical role in identifying and rectifying crisis events, so be sure to conduct an annual crisis simulation with them. This dress rehearsal will help you quickly identify any holes in your plan and fix them. So when your crisis breaks at 4 a.m. on a Sunday morning (a la TOMS), the right people will know exactly what is expected of them.
3. Do we have our ears adequately to the ground?
You’ve assessed the threat landscape and developed plans for the correct scenarios, but does your team have the tools to keep tabs on social discussions that involve your brand? Social listening is a critical communications discipline in today’s environment, as it gives your team a full view of the sentiment and scope of what is being said online about your brand. With a program in place that can inform your organizations’ response, you’ll save precious time and be in a better position to manage the crisis.
4. Do we have the right coverage?
Whether it’s process, platform, or software, there are more options than ever when it comes to building an arsenal of protection for your business’s data. No longer are data breaches the sole domain of technology companies, banks, and retailers. The growing ransomware trend, which motivated Baltimore’s cybersecurity move, means any organization that maintains data is now at risk. Communicators need to be prepared with the right strategies and, when necessary, the right tools. So what will your action plan be if someone holds your data hostage and what tools could help you prevent it?
Long after the details of a crisis are forgotten, the effects of how your organization responds will still be felt. If you need help planning for new threats or are looking to augment your plans with resources to better identify potential issues, contact us here.




